Is cryptography the future of physical access control?
17 May, 2010
category:
 PKI begins its migration from the desktop to the door
PKI begins its migration from the desktop to the door
By Zack Martin, Editor, AVISIAN Publications
Most people don’t think much about opening doors: insert key, turn knob and walk in. If your workplace issues ID badges there may be a bit more thought that goes into it as you tap the badge on a sensor, hear the click and pull open the door.
But physical access systems are undergoing the most radical transformation since the switch from keys to cards and tumblers to electronics. To the end user very little should change–there may be an increase in the use of biometrics–but most individuals will still simply tap the ID and go.
It’s what happens behind the scenes that will be vastly different. Backend system will drastically change. Access control readers and controllers will become more sophisticated with cryptography and bi-directional communication. Because physical access control systems typically have a lifespan of 10 years, this won’t happen overnight, but industry visionaries agree that it will happen.
Leading the charge for these next generation systems is the U.S. federal government. The FIPS 201 physical access control specification recommends public key infrastructure (PKI) at the door. The specification, Special Publication 800-116, does not mandate PKI, but recommends it. This, however, could change as a revision to the original FIPS 201 standards is due by the end of 2010 and some say it could include a PKI mandate (See Predictions for FIPS 201-2).
PKI is typically associated with logical access and digitally signing documents. When it was proposed for physical access it was something of a first. Making the leap wasn’t that difficult though, says Bill MacGregor, a computer scientist at the National Institute of Standards and Technology. MacGregor, who was instrumental in writing Special Publication 800-116, says there were simply too many points of potential vulnerability with existing physical access systems.
“We knew there were a significant number of plausible threats against physical access control solutions dealing with authentication,” MacGregor says. “There are devices available on eBay that would duplicate many of the common cards used for physical access control.”
That’s one of the reasons why the FIPS 201 spec released in 2005 limited the applications for the contactless interface and prohibited its use with biometrics and other sensitive data. It’s also a reason many experts say that portion of the standard is incomplete and potentially even insecure.
The cardholder ‘s unique ID number is stored on the contactless portion of the card and it’s possible for it to be read and copied. “This is more or less a step above a prox reader,” says Rob Zivney, vice president of business development at Hirsch Electronics. “To get the real benefit of FIPS 201 you need to do better than a basic read of the cardholder unique ID, you need to go to PKI.”
In order to properly secure systems and provide high-assurance authentication, the government needed to apply cryptography, MacGregor says. Since FIPS 201 was already using smart cards and PKI for logical access it seemed like a logical leap to use it on the physical side of things too. “PKI is a fully standardized, mature technology and it’s deployed through the Federal Bridge,” he says. “And it forms the core of the trust model for the PIV credential.”
While using PKI for physical access control might be new, the technology is not, says Sal D’Agostino, CEO at IDmachines. That it’s been around for some time and there are standards around it means not having to reinvent the wheel. “It’s strong security, standards based, open and through a federation it enables trust and interoperability,” he says.
But there are still serious questions, including how long it takes to process a transaction and how it will affect existing physical access control infrastructures.
How it will work
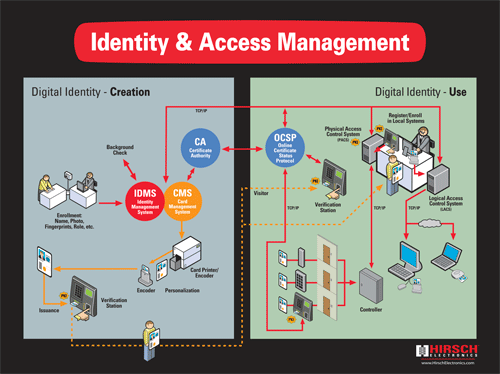
In a PKI at the door implementation, as in traditional access control systems, the first thing that will happen is registration into the system. At this point in the FIPS 201 environment, the contact interface of the credential will be used to check the PKI certificate, PIN and fingerprint biometric template stored on the card.
This process currently takes between 13 and 30 seconds and will have to be performed whenever the credential is to be used in another physical access system. For example, a State Department employee going to a Homeland Security office will need to have his credential registered into the system before it can be used.
After that initial registration the cardholder can use the contactless interface to have the PIV authentication key, one of the four PKI certificate on the card, checked. This process, along with the usual challenge and response that takes place with contactless smart card transactions, currently takes one to three seconds.
First, however, the existing infrastructure for most physical access systems would have to be upgraded. Typical access control systems use the Weigand protocol to communicate with controllers. Weigand is a one way communication, says David Auman, partner at ID Technology Partners. But for PKI to work there needs to be a back and forth with the system. “Current systems are designed to send an ID number and not much more,” he says. “But if you want to do authentication you need bi-directional protocols which you get with a network.”
PKI at the door will require Internet Protocol-based access control devices, Auman says. “When you bring session encryption and mutual authentication you need an IP-based device just to get the connection,” he says.
Putting physical access control systems online raises security concerns to some, but just because you IP-enable a system doesn’t mean it’s available via open networks, Auman says.
The physical access readers and controllers will also have to undergo a makeover with PKI at the door, says Hirsch’s Zivney. There will be two choices for the architecture of new physical access systems: do the processing of PKI certificates at the reader or do it at the controller. Either way the processor on the device that is chosen will need additional cryptographic certification.
Most likely the choice will be to go with a smart controller instead of a smart reader, Zivney says. “The argument is that there’s too much risk in putting the intelligence on the unsecure side of the wall,” he says.
Wave and go vs. hold and go
While upgrading the infrastructure for physical access control systems will be time consuming and costly, a bigger concern with PKI at the door is how long the transaction will take. Experts say it could take as long as a second and a half to open a door. This may not seem excessive but imagine trying to get through a turnstile with hundreds of other employees in the morning. Some fear that transaction duration could be the deal breaker in many environments.
Others disagree. “It’s the difference between wave and go and touch and go,” says D’Agostino. “It does require some crowd behavior effort, but just as people learned how to get on and off an escalator they’ll learn how the system works.”
Symmetric vs. asymmetric keys
To deal with the time issue some are suggesting a switch from PKI, or asymmetric keys, to a symmetric key scheme, says MacGregor. “People say that symmetric keys are faster than PKI at the door,” he says.
But PKI is more secure and may actually be easier to deploy and manage than symmetric keys, MacGregor says. With PKI the secret is stored on the card and it never leaves that card. There is a public certificate on the physical access control system but it’s not a secret. “It’s widely distributed and there is no security vulnerability,” he says.
With symmetric keys the same certificate stored on the card also has to be stored on the physical access control system. This leads to more complex key management than with PKI. “Public keys don’t need to be protected,” MacGregor says, “but all these symmetric keys need to find their way to a reader on a door and must be protected in transit, in use and at the reader.” This results in far more vulnerable situations and more opportunities for system compromise.
Symmetric key management can be expensive and complex, especially when dealing with something the size of the federal government, says MacGregor. “A fact of large scale use is that key management drives the cost,” he says. “It’s expensive.”
While symmetric keys may bring a speed advantage the complexity of key management may be too much of a detractor.
Making PKI work at the door without the wait
The General Services Administration has been pursing an expedited PKI at the door solution. The agency contracted with Exostar, a provider of collaboration solutions for the aerospace and defense manufacturers and their 40,000 supply chain partners and CertiPath, a credentialing authority for aviation, aerospace and defense organizations.
The concept demonstrates how a single-credential system can provide secure access for both physical and logical assets, while also providing interoperability for employees, customers and partners. The need for the system arose for the greater security needed for federal physical access control systems, says Steve Howard, vice president of operation at CertiPath.
The system demonstrates the ability to perform the challenge response to the card authentication key on the contactless portion, but also how the system works with the contact portion including use of the biometrics and PIN, Howard says.
Additionally, it addresses ways to handle guests with and without PIV credentials, Howard says. A visitor with a trusted credential can use it to pre-register via a Web site for a remote visit request. Upon arrival at the site the card has already been verified and after checking in the visitor can gain access to protected areas.
Guests that do not have a trusted credential check in at an attended area and are issued a credential with an operational biometric and PKI certificate stored on the card, Howard says. “Now every defined population is using PKI for physical access control,” he says.
CertiPath’s architecture conforms to the principles of NIST Special Publication 800-116 and also:
- Leverages PIV, PIV-I, the Department of Defense Common Access Card and the Transportation Worker Identity Credential
- Utilizes FIPS 201-certified, or in process, components
- Enables customers to upgrade without replacing existing systems
- Leverages commercially available products to minimize custom solutions
- Uses the U.S. Federal Bridge to validate interagency trust
- Delivers cost-effective options to operate at one or multiple assurance levels
‘Caching’ in on PKI
HID Global is working to improve the speed of PKI at the door via caching, says David Adams, senior product marketing manager at the company. The company’s caching status controller checks the certificate on the card once and then conducts periodic checks back to the revocation list to make sure the certificate is still valid.
Initially the cardholder taps the badge on a reader, Adams says, and the PKI certificate on the card is checked against the Federal Bridge, a process that takes a couple seconds. From that point forward, the certificate is checked against the stored cache that is updated every hour against the Federal Bridge.
In essence, at set time intervals the system validates the certificates from all cards commonly used in that specific access control environment. When a card is presented at an access reader, it need only be validated against the local cache, a process that is much quicker than validating against the remote system.
“You’re extending the Federal Bridge right out to the door,” Adams says. “Then you get virtually the same card performance as you do with a standard transparent reader and you’re going with a smart, very secure edge appliance to do it.”
Meet MR-PIV
ID Technology Partners has created a solution for physical access control called Mutual Registration PIV, or MR-PIV, that speeds up transactions and potentially makes them more secure, says Auman.
The solution enables a credential holder to register the card in the local physical access control system and also register that system with the card, Auman says. That way if anyone tries to sniff information off the card and the system doesn’t have that mutual registration the card won’t give up any information. Also, since it’s a local identifier and not the global identifier the process is quicker.
“Rather than register the global identifier of the card we register the local identifier and a key to the physical access control system,” Auman says.
This mutual registration speeds up the transaction to around half a second, Auman says. “The throughput is a five or six times performance increase,” he says.
The role of biometrics in physical access
While it seems clear that PKI at the door is coming, not as clear is the role that biometrics will play with these new systems. Biometric authentication is the single best way to truly tie the credential to the holder.
“Biometrics are an intrinsic property of the owner,” says NIST’s MacGregor. “It adds to the high assurance and the non-transferability of the credential.” This will become increasingly important as other weaknesses in physical access control systems are alleviated.
In a PIV card system the contact interface of the card contains two fingerprint templates that can be used to confirm identity. These would be used to register into a new physical access control system. However, since the contactless interface doesn’t have access to these templates, it would be difficult to use the biometric anywhere that high throughput is necessary.
When a biometric authentication is required, would depend on the security policy of the particular agency. They wouldn’t have to be used by credential holders on a daily basis.
D’Agostino says biometrics must begin to play more of a role in physical access control. “PINS are a pain,” he says. “Biometrics is much easier than PIN and it’s the preferred second factor.”
Turf war
While general consensus seems to be that PKI at the door is the future for physical access control there are still challenges. One of the biggest maybe convincing those on the IT side and those on the physical security side to cooperate, says MacGregor. “It does require governance to talk about change management,” he says.
But change is happening as the industry works to make it easier for the authorized to gain entry while making it more difficult for the unauthorized to circumvent systems. The changes won’t happen overnight and won’t come without pain, but in the end security will be improved.
Predictions for FIPS 201-2
Every five years federal information processing standards (FIPS) are up for revision and since it’s been half a decade since FIPS 201 was released discussion on what may be included in an update is underway.
It’s difficult to say what may be included this early in the year, but experts are focused on five areas.
PKI at the door
Even though many vendors and government officials suggest PKI for physical access control is the next big thing, FIPS 201 doesn’t mandate it. NIST Special Publication 800-116 recommends PKI at the door but many say it could be mandated in the revised FIPS 201 specification.
Contactless
The contactless capability was purposefully limited in the first standard and this has been an ongoing criticism of the first spec. Many from the physical security realm would like to access biometrics over the contactless interface, a practice that is currently prohibited. Perhaps an easing of these limitations is on the horizon.
Match on card
Officials posit that match-on-card fingerprint biometrics could be included in the revised spec. With match-on-card technology the fingerprint template never leaves the card and the match is conducted on the card itself, rather than a reader or controller.
Iris
Iris biometric standards have improved in the past five years and the proprietary nature of the technology has eased. Some predict it will be added as an additional biometric modality for FIPS 201.
Adding trusted applications
Another criticism of FIPS 201 is that it basically sealed off the card after issuance. Agencies that wanted to add another application, such as e-purse, haven’t been able to do it. A revised FIPS 201-2 may include the ability to add trusted applications to the card to increase its usability.
Beyond convergence and PKI: Fusion
PKI at the door may be coming and most have heard about the convergence of physical access and access to computer networks using one credential, but beyond that is what some are calling fusion.
Fusion may be the ultimate end game of PKI at the door and convergence. Once physical access control readers and IT networks are wired together it will enable the systems to do things never before possible and have far greater intelligence, says Bill MacGregor, a computer scientist at the National Institute of Standards and Technology. “Information can be shared across the physical and logical worlds,” MacGregor says.
“A parallel would be with fraud detection in retail practices,” MacGregor says. “We are all used to the idea that if we travel somewhere and use a payment card there might be questions.”
Similarly, fusion would enable a system to question why someone is using a badge for physical access in San Francisco when they are logged on to a computer in Chicago or even using the phone in another location. Such a system could also track when an employee walks in the front door, only then enabling him to login to secure computer networks.
Defining the terms:
Symmetric key cryptography
In a symmetric key system the same encryption key is used to both encrypt and decrypt a message. Thus both the sender and the recipient must be in possession of the shared, secret key. In the case of a physical access control system using symmetric keys, this key sharing leaves both the cards and the system as points of vulnerability. Examples of common symmetric key systems include AES and DES.
Asymmetric key cryptography
In an asymmetric system, a matched pair of encryption keys–one public and one private–is issued for each credential or user. Data encrypted using one key from a pair can only be decrypted using the pair’s other key. The power of an asymmetric system is that a user’s private key never leaves his possession. Unlike a symmetric system, there are no shared secrets in asymmetric cryptography and thus vulnerabilities are greatly reduced. Public key cryptography is synonymous with asymmetric cryptography.
Public Key Infrastructure (PKI)
PKI is a specific implementation of asymmetric cryptography. It relies on the use of digital certificates that are issued by certificate authorities as a means to bind a user to an assigned key pair. In other words, a trusted third party (the certificate authority) vets the identity of the individual owning the key pair and then issues a document (the digital certificate) asserting this fact. In use, others can have confidence in the identity of a key pair’s owner by verifying the authenticity of the digital certificate.
Federal Bridge
The Federal Bridge Certification Authority is a system that facilitates acceptance of PKI certifications for transactions. Since its initial concept and operations, it since evolved into the Federal Public Key Infrastructure Architecture (FPKIA) that encompasses Certification Authorities from multiple vendors supporting different Federal PKI policy and function.