The GSA FIPS 201 Approved Products List redux
05 April, 2011
category:
 The impact of FIPS 201-2, ICAM, PIV-I, NSTIC
The impact of FIPS 201-2, ICAM, PIV-I, NSTIC
By Salvatore D’Agostino, CSCIP, IDmachines LLC
A little over a year ago IDmachines reviewed the FIPS 201 Government Services Administration (GSA) Approved Products List (APL) also known as FIPS 201 Evaluation Program Products and Services.
FIPS 201, Personal Identity Verification (PIV), has just been updated with a draft FIPS 201-2. This is part of an coordinated set of identity and cybersecurity activities on the part of the United States government that includes the Federal Identity, Credentialing and Access Management (ICAM) and the National Strategy for Trusted Identities in Cyberspace (NSTIC).
At the time of this post there were 514 products listed. This does not take into account the shared service providers that issue digital certificates that form the basis of the federal government and related commercial public key infrastructure (PKI). PIV credentials have been complemented by the issuance of interoperable credentials for non-Federal government entities by those cross-certified as Personal Identity Verification Interoperability (PIV-) issuers.
Industry continues to make a significant investment in developing products to meet FIPS 201. This should accelerate further with the Office of Management and Budget Memorandum 11-11 which states that each agency is to develop and issue an implementation policy by March 31.
The GSA APL as a program needs to evolve with these changes. We have gone from mandate–Homeland Security Presidential Directive 12–to specification and special publications, to testing program and list of approved products, to physical access control implementation recommendations, for example, National Institute of Standards Special Publication 800-116 (SP 800-116), to the ongoing ICAM efforts.
Some of the wiggle room is disappearing. Many agencies met the mandates by doing the minimum possible, such as putting a 125 MHz coil in their PIV card to support their legacy physical access control system, others simply implemented free reads of an identifier in the clear.
Neither of these is recognized as any level of assurance. Many of the solutions in place for physical access on the wall in agencies will have to be torn out and replaced. In many cases the controllers in the wall will have to be upgraded as well.
A very large market will occur for this upgrade over the next few years, and as you will see on the list below there are still a very small number, sometimes no solutions in place. In addition FIPS 201-2 introduces new techniques such as biometric match on card which will create new categories. In addition to the new categories agencies will have to plan for and acquire the identity infrastructure to support both logical and physical access control.
In general there needs to be a further evolution and rationalization of the testing categories and requirements. The further evolution needs to include specific acquisition guidance, acquisition rules and consistent implementation in particular around identity authentication factors.
This occurs in parallel as industry continues to invest to meet the full set of requirements, at the application, system and infrastructure levels. The APL has thirty categories. The following is a breakdown of the categories along with the number of products listed in each category and the number of companies represented among those products and a comparison with the last summary done by IDmachines.
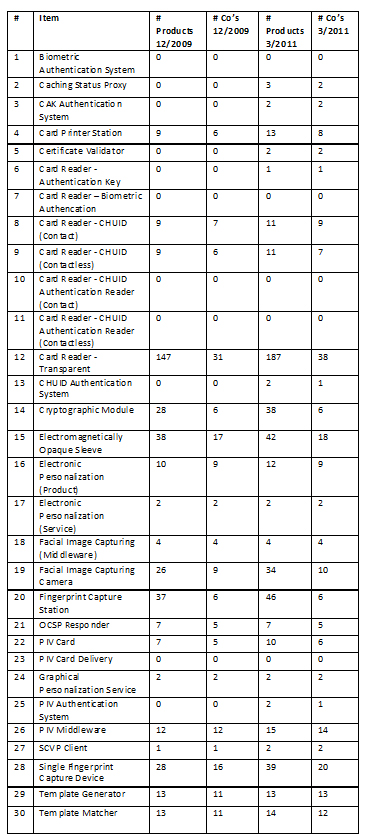
A few items jump out. First, there are only five categories, as opposed to 11 previously, with no products listed. Second, for those categories with products listed all have multiple suppliers with three exceptions. Third, the distribution of products remains heavily geared toward the top categories—around 36% in the top category and roughly 54% in the top three categories and 83% in the top 10.
It makes sense to ask the same question as last time. Does this meet the goals of the program among which are interoperability, improved security and cost savings? And in fact the answer is the same as last time, it is yes and no.
Having a program is crucial. In fact this message needs to be strengthened and should be part of the activity around FIPS 201-2 and NSTIC. It sends a clear message and complements the OMB message that government is serious about HPSD-12–although the OMB memorandum’s teeth have yet to be cut.
There remains a need to test the product categories and also needs testing of systems. An example would be checking to see if the policy behind the issuance of credentials matches that required by the relying parties as specified by Federal policy.
It would be good to expand some of the testing to include characteristics applicable outside the federal enterprise such as the Global Unique Identifier (GUID) and the related Universally Unique Identifier (UUID). There is not yet an approved Cardholder Unique Identifier (CHUID) or biometric authentication system listed. While a new/expanded biometric authentication system exists to include match on card there isn’t any category to test a GUID/UUID authentication system. Updating the categories to match some of these things should be forthcoming and keep pace with the changes.
PIV testing challenges include the availability of test cards, positive and negative and no test for endurance. There have been recent issues, which have hopefully been resolved, around antennas and contactless reading.
Physical access control vendors have encountered PIV cards in agencies that are approved yet are not reading. As lot of the responsibility of this has fallen back to the vendors to prove it’s not a reader issue. Its not surprising this occurred since physical access was an area where PIV cards could be quickly used.
One new characteristic of the GSA APL since the last review is the use of color to highlight categories called out in SP 800-116. There is a lot of work for FIP 201-2 to update its related and supporting special publications and these will impact some test procedures.
These activities will be coordinated with updates to the APL. There remains the extremely important matter in the fact that products are listed independently of the assurance level that they provide unless you connect the category to the relevant document and category.
It remains the case and is not surprising that the category with by far the largest number of products listed–transparent readers–happens to implement the specification and the lowest, and some would say no, possible assurance level.
While it is possible to have a transparent reader working with a stronger authentication machine, ideally secured, in many cases this is not true and the transparent reader is the sole tool for authentication. It still makes a big difference among the ways a product or solution can make the statement that it meets HSPD 12 or FIPS 201 and soon FIPS 201-2.
The education challenge remains for GSA and for NIST to reach out to the agencies and organizations leveraging FIPS 201. The ICAM effort is a big help in this regard. ICAM and FIPS 201-2 need to get outside the beltway to local program officials. There also needs to be a continued collaboration with industry.
Some vendors and integrators have gotten the message; other are just getting the wake up call, fewer are still asleep. Fortunately multiple government and industry organizations are helping in this education effort. The NIST workshop April 18 and 19 should help to further the conversation. Now is an important time to be involved. The GSA APL is an impressive list that represents a lot of good work. We’ll see where it goes from here.


